Skype worm? Not!
This week kicked off with a bang. A worm had been unleashed into the ‘net, targeting the users of Skype for Windows. You can check out Villu Arak‘s post in Skype’s Heartbeat blog to read more about the worm and how to protect yourself from similar attacks in future.
Phil Wolff posted a nice, but oversimplified graphic explanation in Skype Journal:
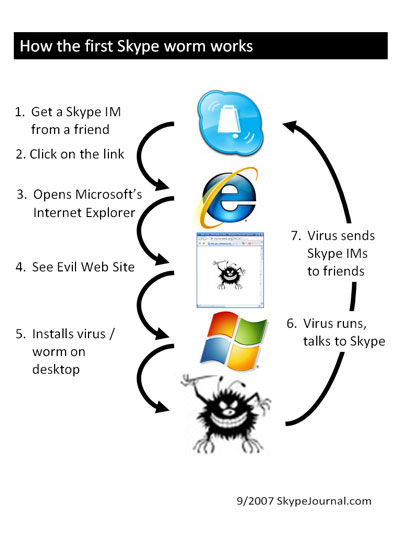
Why is this oversimplified? Because this explanation fails to address probably the most important point given in Villu’s post:
Please note that Skype users ONLY become infected after they have downloaded the link and run the malicious software.
Step 2 (clicking on the link) would probably not happen if the user would think twice, considering the language (and style) of the message. How likely is a serious business associate to send you a message like “hey i’ve found ur pix on the net”?
Step 3 (opening MS Internet Explorer) would probably not happen if the user would have had chosen a better browser (e.g. Firefox) as default.
Step 4 (seeing evil website, or actually a prompt to download a .scr (Windows screen saver) instead of a .jpg image) would probably not happen if the user would take a second look at what he’s being offered.
Step 5 (installing the worm) would definitely not happen if the user had at least half a brain and basic elements of common sense. Or if s/he would have used Skype on Mac or Linux, because Windows screensavers don’t work on these platforms.
Running a freshly updated antivirus product would probably have helped a bit as well. But even the best antivirus does not replace your missing common sense. Or do you really think wearing a condom keeps you 100% safe when having sex with strangers?
It was not a Skype worm, because Skype didn’t get infected. It was a Windows worm. Or rather, a Windows dumbuser worm.
NOTE: The opinions expressed in this post are my own, and must not be interpreted as those of my present, past, or future employers.